微信小程序用戶信息解密失敗導致的內存泄漏問題
發布時間:2018-05-29 11:17 所屬欄目:小程序開發教程
微信小程序獲取用戶解密的Session_key 然后對 encryptedData進行解密 偶爾報錯 時間長了之后會報內存溢出:
- java.lang.OutOfMemoryError: GC overhead limit exceeded
- at javax.crypto.JarVerifier.verifySingleJar(JarVerifier.java:426)
- at javax.crypto.JarVerifier.verifyJars(JarVerifier.java:322)
- at javax.crypto.JarVerifier.verify(JarVerifier.java:250)
- at javax.crypto.JceSecurity.verifyProviderJar(JceSecurity.java:160)
- at javax.crypto.JceSecurity.getVerificationResult(JceSecurity.java:186)
- at javax.crypto.Cipher.getInstance(Cipher.java:653)
看代碼是java解密的時候報錯了,
然后將老代碼
- public byte[] aesCbcDecrypt(byte[] content, byte[] keyBytes, byte[] iv) throws NoSuchPaddingException, NoSuchAlgorithmException, InvalidAlgorithmParameterException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException {
- //密鑰
- SecretKey k = new SecretKeySpec(keyBytes, "AES");
- Security.addProvider(new org.bouncycastle.jce.provider.BouncyCastleProvider());
- Cipher cipher = Cipher.getInstance("AES/CBC/PKCS7Padding",
- new BouncyCastleProvider()
- );
- cipher.init(Cipher.DECRYPT_MODE, k, new IvParameterSpec(iv));
- //執行操作
- return cipher.doFinal(content);
- }
改成如下方式
- private static Provider provider = new BouncyCastleProvider();
- public byte[] aesCbcDecrypt(byte[] content, byte[] keyBytes, byte[] iv) throws NoSuchPaddingException, NoSuchAlgorithmException, InvalidAlgorithmParameterException, InvalidKeyException, BadPaddingException, IllegalBlockSizeException {
- //密鑰
- SecretKey k = new SecretKeySpec(keyBytes, "AES");
- Security.addProvider(new org.bouncycastle.jce.provider.BouncyCastleProvider());
- Cipher cipher = Cipher.getInstance("AES/CBC/PKCS7Padding", provider);
- cipher.init(Cipher.DECRYPT_MODE, k, new IvParameterSpec(iv));
- //執行操作
- return cipher.doFinal(content);
- }
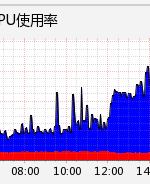
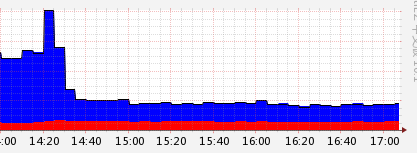
用Jmeter 100并發壓測 可以檢測到老代碼內存在上升然后短時間不會釋放,新代碼上升然后穩定(和知乎文章鏈接中的結果一致),而且新代碼運行速度也更快(不用每次都new了)。
老代碼cpu:
新代碼cpu:
微信服務器返回的數據為什么解密失敗,這個原因還是待查。同一個用戶,前兩次解密失敗,Session_key不變,然后第三次可以成功。
實時分析java占用cpu的進程及線程,找到線程對應的java代碼。
top -Hp pid
jstack pid下的線程pid
參考了微信中的文章
但是貌似并不是所有的問題代碼都能在里面定位到。